The AME Group collaborated with Evolve for a panel discussion on Cyber Liability Insurance for Manufacturing. Here what Jack Bowden with Evolve MGA says are the reasons manufacturers need cyber insurance.
Your security is only as strong as the training of your employees. All it takes is one employee clicking on what appears to be an innocent link, but it’s actually malware. In seconds, your data is encrypted. Next, a hacker will contact you asking for a ransom ranging from a few thousand dollars to millions to decrypt the files. This is the most prevalent attack today and is used against every industry and size.
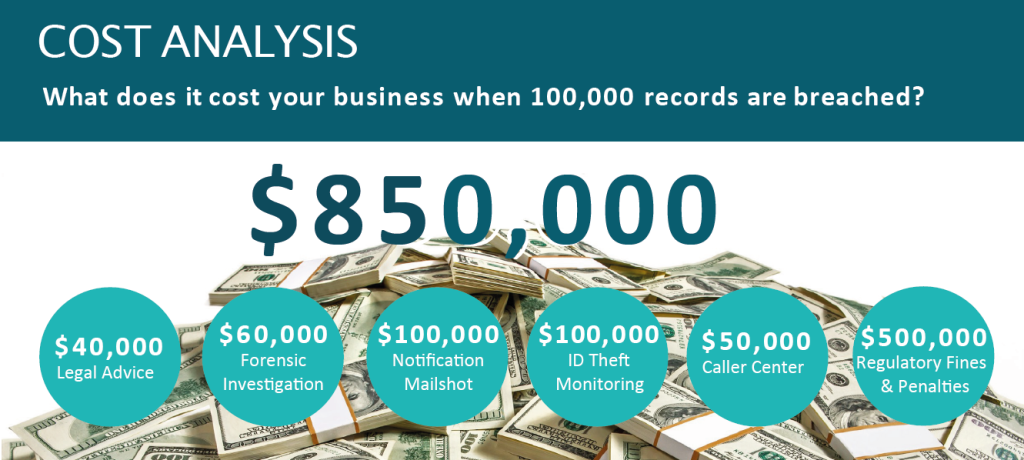
Should there be a cyber attack, you will need to engage a forensic investigator ($250-$500/hr) to determine the scope of the attack. Is any sensitive data such as employee or client records breached? If so, a law firm will get involved to notify individuals and regulatory body according to legal responsibly. Cyber insurance agencies have teams on hand to help you navigate the process.
According to Kaspersky Lab, an international software security group, one in every five manufacturing businesses has lost intellectual property to a security breach within the past year alone.
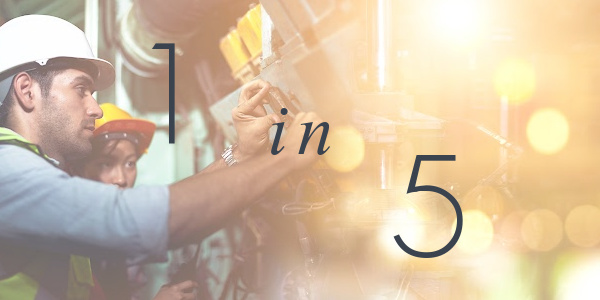
Manufacturers like you rely heavily on computer systems. Damage to your systems can be devastating. It can lead to defective products or halt in production. The investigator will identify what went wrong. Then, you will engage your IT team to eradicate the malware and repair the systems.
You will experience a direct financial loss every hour your systems are down. You can incur unexpected costs such as sourcing products by alternative means and paying staff overtime to meet deadlines. Additionally, manufacturers of non-durable goods could see a loss in profit as inventory spoils during the outage.
Social Engineering is one of the most frequent claims in cyber insurance to date. Cyber criminals trick financial department employees to send money to fraudulent back accounts. Hackers are patient and will sit in your system undetected monitoring and intercepting email activity before executing their scam. Tactics range from posing as the CEO, a vendor, or client to creating fake employee profiles in the payroll system to siphon money out.
Check out our Breach Cost Calculator to learn more.
619 Main St
Vincennes, IN 47591
812.726.4500