
In a Business Email Compromise is also know as a BEC scam, or email account compromise (EAC). It’s when criminals send an email message that appears to come from a known source making a legitimate request.
Every week this month we’ve assisted a business with a breach caused by stolen email credentials. It is by far the most lucrative attack for cybercriminals.
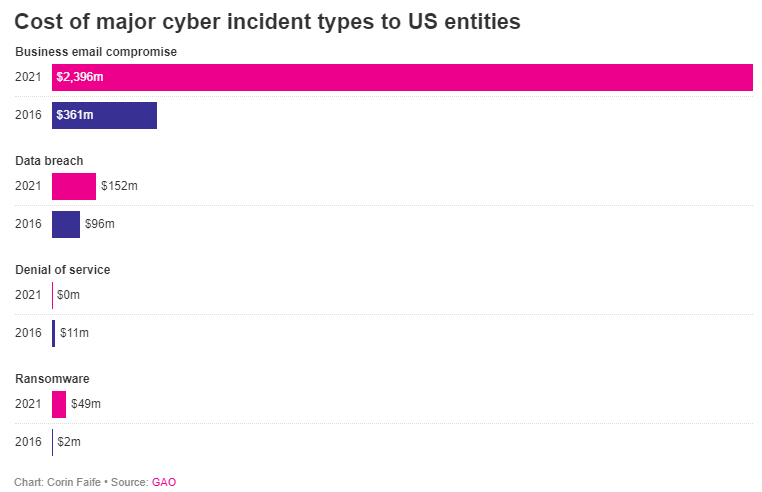
Businesses need to start taking cybersecurity more seriously, as one government agency is warning that ignorance of best practices can lead to “catastrophic financial loss.” The U.S. Government Accountability Office is worried that insurance may soon not be able to cover the losses. The GAO lists the cost of BEC to America businesses to be over $2.3 billion.
Back to the businesses we’ve helped this month. None of them had Multi-factor Authentication in place.
MFA is built into Microsoft and the other large email providers. This one step can easily save you over $100,000 to repair the damage of BEC. This why insurance providers REQUIRE MFA before allowing you to purchase a cyber liability policy that covers email compromise.




An employee traveled for work and used a parking app. His username was his work email. His password was his work password. The parking app was breached. Cybercriminals started trying the stolen passwords to log into office.com. His username and password worked! They are now checking out business email activity and learning what will be the most lucrative target.
This is how cybercriminal redirect payments. Or a common but still successful scam – asking an employee to purchase gift cards or send W-9.
The cost is high.
The risk is high.
MFA is easy.
619 Main St
Vincennes, IN 47591
812.726.4500