
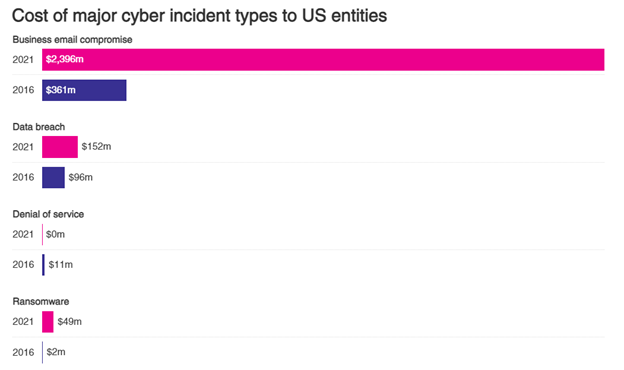
In 2021, America experienced an unprecedented increase in cyber attacks and malicious cyber activity. Business Email Compromise is the most frequent attack vector. The FBI received nearly 20,000 complaints in 2021 that cost US businesses 2.4 billion. In 2023, it was nearly 22,000 with a $2.7B in losses. The second most costly digital crime type, investment scams, tallied about $1.5 billion in estimated losses. Your email account is an important part of your communication with employees, customers, and vendors. It’s often the everyday information that opens your business to attack, like who approves purchases, what applications you use, how you communicate with each other. If this information gets into the wrong hands, that could mean big problems for you and your business.
Let’s say you use a cloud hosted application for HR and payroll. You have recently changed your password and can’t remember it any longer. So, you click on the forgot password link and the service sends you a link to reset it. Now you can log in and get to work so everyone gets paid on time. What you didn’t know is someone gained unauthorized access to your email account, and they see the same emails you see. Now they know what payroll application you use.
Before the act, they setup a few things so you don’t know what they are doing. First, many attackers create a forward rule on your email to send all incoming email to their account. Another tactic is to create a mailbox rule that deletes some or all messages after forwarding it, so you never even see the email. It’s also common for attackers to use your email account to send highly relevant email content to others in your organization. This might gain them access to other accounts or further the success of their attack.
Now that their actions are hidden, they use the ‘forgot password’ link on your application. The reset instructions are emailed to you, immediately forwarded to the attacker, and deleted from you email. You never know this happened. The attacker then logs in, finds contact info for multiple employees, and starts emailing them from your account asking them to click the link below to login and review their pay settings so a special bonus can be provided to their paycheck. Unfortunately for them, the link is to a specially crafted web page that steals the employee’s login credentials to the payroll system. Now the attacker starts changing direct deposit information to send payroll checks to a bank account they own. Before you know it, thousands of dollars have gone to the attacker’s bank accounts. The attacker then moves the money to leave accounts empty or closed.
This is just one example of a recent email compromise. We respond to businesses experiencing this type of activity almost weekly. What other information is transmitted in your email that if compromised would put you or your business in jeopardy?
There are ways to prevent an email compromise attack, some that can be accomplished with relative ease and little cost.
The faster the employee can respond, the less the loss and the cost. As simple as calling instead of emailing when something is suspicious. An email may never be received. There are many options available to train your staff to be aware of threats and act when something is not right. You can start by becoming a National Cybersecurity Awareness Champion (October) – learn more at Cybersecurity Awareness Month – National Cybersecurity Alliance (staysafeonline.org) and CyberSecure My Business™ – Stay Safe Online (wpengine.com)
MFA should be enabled on all email accounts and cloud applications. This would have prevented the attacker from gaining access to the email account to begin with and prevented the further breach of payroll. Most applications now have MFA, like Microsoft Office.
The user in our scenario above would not have forgotten his password which may have prevented the attacker from even knowing the cloud payroll system existed.
Don’t provide permission to access functions or features of an application unless necessary for them to perform their assigned role.
One individual may be able to make a change, but another individual must approve it in the system before it is authorized, a two-step authorization process. Many applications support this approach.
This greatly reduces the available footprint for an attacker to work with.
SSO service that verifies user identities before their accounts can be used to gain access to applications or other business resources.
Monitor and receive alerts for malicious or suspicious activity in your network, systems, and applications. SIEM applications/services for monitoring and alerting and Security Operations Center to respond and eliminate the threat a requirement in today’s electronic world.
SECURITY AWARENESS TRAINING PLATFORM
How to recover a hacked or compromised Microsoft account
What You Should Know About Account Takeovers
Cost of Business Email Compromise
NIST Small Business Cybersecurity Corner

reversal and a Hold Harmless Letter or Letter of Indemnity.
provided fields, including banking information.
specific populations, like trends targeting real estate, pre-paid cards, and W-2s, for example.
619 Main St
Vincennes, IN 47591
812.726.4500